- Vmware Hyperthreading Unmitigated Tool
- Vmware Hyperthreading Mitigation
- Vmware Hyperthreading Unmitigated Usb
- Vmware Hyperthreading Mitigation
- Vmware Vsphere Esx.problem.hyperthreading.unmitigated
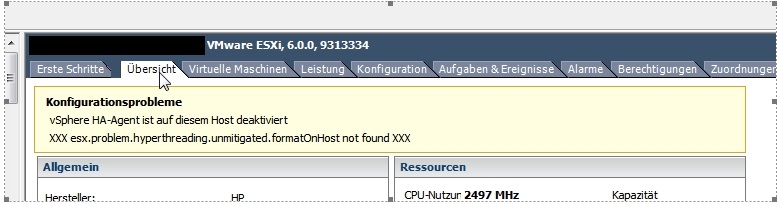
Novice VMware admin here looking for some advice. I know there is much debate about hyperthreading and the real answer is it depends on your system and applications you're running. I've got a few small clusters mostly running Windows 2016 for the essentials: Active Directory, DHCP, DNS, File/Print, WSUS, Veeam, Mitel and a few pretty light on. After applying the patches (Aug 14, 2018), a warning message showed on patched ESXi hosts: esx.problem.hyperthreading.unmitigated According to the release notes, VMware introduced a new Advanced Configuration on the hosts to mitigate the new hyperthreading attacks, however, it states there's a performance hit that cannot be ignored.
The purpose of this article is to provide an overview of the security issues related to speculative execution in Intel processors described by CVE-2018-3646 (L1 Terminal Fault - VMM), CVE-2018-3620 (L1 Terminal Fault - OS), and CVE-2018-3615 (L1 Terminal Fault - SGX) as they apply to VMware products. Because there will be multiple documents necessary to respond to these issues, consider this document as the centralized source of truth for these issues.Vmware Hyperthreading Unmitigated Tool
The Update History section of this article will be revised when there is a significant change to any of the related documentation. Click Subscribe to Article in the Actions box to be alerted when new information is added to this document and sign up at our Security-Announce mailing list to receive new and updated VMware Security Advisories.
To assist in understanding Speculative Execution vulnerabilities, VMware previously defined the following categories in KB52245 and KB54951 - here is a brief summary of these four categories:

- Hypervisor-Specific Mitigations prevent information leakage from the hypervisor or guest VMs into a malicious guest VM. These mitigations require code changes for VMware products.
- Hypervisor-Assisted Guest Mitigations virtualize new speculative-execution hardware control mechanisms for guest VMs so that Guest OSes can mitigate leakage between processes within the VM. These mitigations require code changes for VMware products.
- Operating System-Specific Mitigations are applied to guest operating systems. These updates will be provided by a 3rd party vendor or in the case of VMware virtual appliances, by VMware.
- Microcode Mitigations are applied to a system’s processor(s) by a microcode update from the hardware vendor. These mitigations do not require hypervisor or guest operating system updates to be effective.
Mitigation Category Summary for current Speculative Execution Issues:
- CVE-2018-3646 (L1 Terminal Fault - VMM)
Mitigation of CVE-2018-3646 requires Hypervisor-Specific Mitigations for hosts running on Intel hardware.
- CVE-2018-3620 (L1 Terminal Fault - OS)
Vmware Hyperthreading Mitigation

Mitigation of CVE-2018-3620 requires Operating System-Specific Mitigations.
- CVE-2018-3615 (L1 Terminal Fault - SGX)
CVE-2018-3615 does not affect VMware products and/or services. See KB54913 for more information.
Vmware Hyperthreading Unmitigated Usb
This article documents the Hypervisor-Specific Mitigations required to address CVE-2018-3646 (L1 Terminal Fault - VMM) in vSphere.The Update History
 section of this article will be revised if there is a significant change. Click Subscribe to Article in the Actions box to be alerted when new information is added to this document and sign up at our Security-Announce mailing list to receive new and updated VMware Security Advisories.
section of this article will be revised if there is a significant change. Click Subscribe to Article in the Actions box to be alerted when new information is added to this document and sign up at our Security-Announce mailing list to receive new and updated VMware Security Advisories.Introduction to CVE-2018-3646
Intel has disclosed details on a new class of CPU speculative-execution vulnerabilities known collectively as “L1 Terminal Fault” that can occur on past and current Intel processors (from at least 2009 – 2018) [See Table 1 for supported vSphere processors that are affected].
Like Meltdown, Rogue System Register Read, and 'Lazy FP state restore', the “L1 Terminal Fault” vulnerability can occur when affected Intel microprocessors speculate beyond an unpermitted data access. By continuing the speculation in these cases, the affected Intel microprocessors expose a new side-channel for attack. (Note, however, that architectural correctness is still provided as the speculative operations will be later nullified at instruction retirement.)
CVE-2018-3646 is one of these Intel microprocessor vulnerabilities and impacts hypervisors. It may allow a malicious VM running on a given CPU core to effectively infer contents of the hypervisor's or another VM's privileged information residing at the same time in the same core's L1 Data cache. Because current Intel processors share the physically-addressed L1 Data Cache across both logical processors of a Hyperthreading (HT) enabled core, indiscriminate simultaneous scheduling of software threads on both logical processors creates the potential for further information leakage. CVE-2018-3646 has two currently known attack vectors which will be referred to here as 'Sequential-Context' and 'Concurrent-Context.” Both attack vectors must be addressed to mitigate CVE-2018-3646.
Attack Vector Summary
- Sequential-context attack vector: a malicious VM can potentially infer recently accessed L1 data of a previous context (hypervisor thread or other VM thread) on either logical processor of a processor core.
- Concurrent-context attack vector: a malicious VM can potentially infer recently accessed L1 data of a concurrently executing context (hypervisor thread or other VM thread) on the other logical processor of the hyperthreading-enabled processor core.
Vmware Hyperthreading Mitigation
Mitigation Summary- Mitigation of the Sequential-Context attack vector is achieved by vSphere updates and patches. This mitigation is enabled by default and does not impose a significant performance impact. Please see resolution section for details.
- Mitigation of the Concurrent-context attack vector requires enablement of a new feature known as the ESXi Side-Channel-Aware Scheduler. The initial version of this feature will only schedule the hypervisor and VMs on one logical processor of an Intel Hyperthreading-enabled core. This feature may impose a non-trivial performance impact and is not enabled by default. Please see resolution section for details.
Vmware Vsphere Esx.problem.hyperthreading.unmitigated
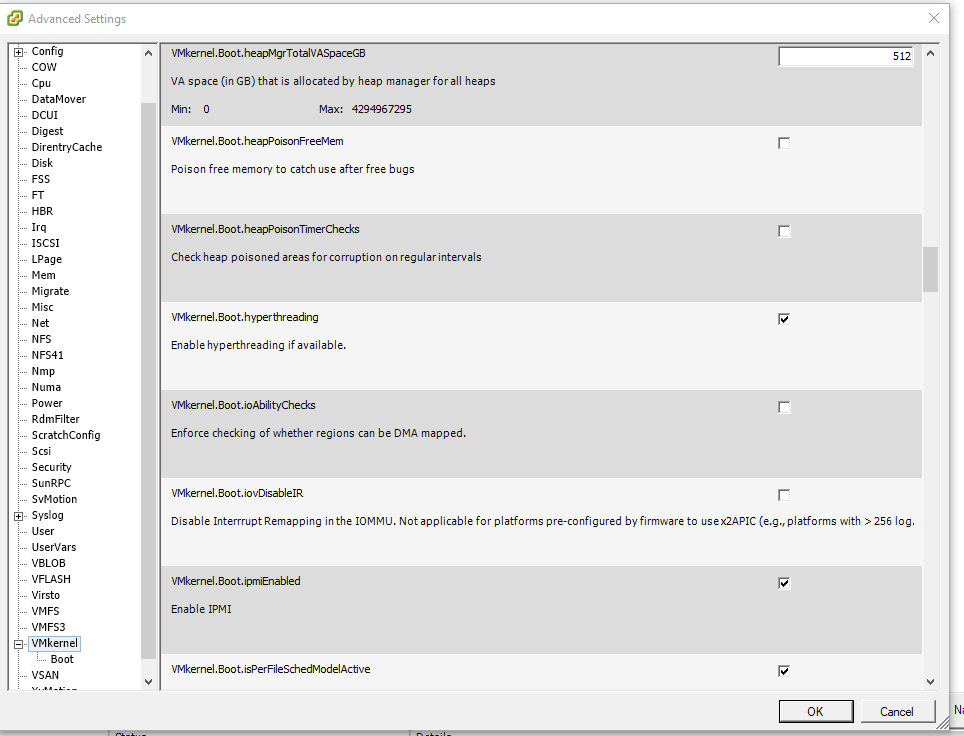
Important: Disabling Intel Hyperthreading in firmware/BIOS (or by using VMkernel.Boot.Hyperthreading) after applying vSphere updates and patches is not recommended and precludes potential vSphere scheduler enhancements and mitigations that will allow the use of both logical processors. Mitigation should be done by enabling the ESXi Side Channel Aware Scheduler (see below).Unlike explicit disabling of Intel Hyperthreading in firmware/BIOS (or by using MKernel.Boot.Hyperthreading), the side channel aware scheduler enablement will be ignored on AMD processors and newer Intel processors that are not vulnerable to L1TF-VMM. [See Table 1 for supported vSphere processors that are affected].
